Instructions for generating an electronic signature key. Instructions for generating the electronic signature key Create a certifying center
Today we will talk about:
- the interesting the topic of cryptography and electronic signature today;
- what regulations are currently operating on this topic;
- what are the possibilities of cryptography implemented in the 1C platform;
- how to expand these possibilities using external components;
- let's talk about the subsystem "Electronic Signature" in BSP;
- about the implementation of services "1C-Edo" and "1C: DirectBank", the development of which I oversaw;
- we will touch on the issue of developing our own solutions to work with cryptography on the 1C: Enterprise platform;
- consider the typical problems that arise on the introduction of Edo in the enterprise - I will tell you how to solve them.
I want to pay attention to the two terms that will be used in the master class.
- The first is Edo, electronic document flow. Under it, we understand the internal electronic document flow in the enterprise, and external with third-party counterparties.
- The second abbreviation is EP. On the Internet there are decodents: "Electronic Government" and "Electric Drive". We will have it electronic signature.

Why do cryptography and electronic signatures are relevant to the current moment?
- For modern enterprise the speed of business processes is one of the competitive advantages.. When applying electronic document management, time spent on statistics decrease by 75%.
- When switching to electronic document proceit occurs saving our own resources (paper cartridges for printers, documents for storing documents, staff time on the organization of paper document management). All this strongly helps the company.
- Almost every enterprise now uses remote banking channels, and security of remote payments Currently very relevant.
- All major taxpayers now include the abstracts that if you want to work with them - share documents in electronic form. Everything goes into an electronic- Electronic invoices, electronic orders, etc. Want to participate in the auction - you should have an electronic signature.
- All this is gradually becomes massBut, despite this, our population is not informed. This represents a serious omission, and therefore the purpose of this review is to ask you a course that will help to navigate in these issues and figure out what can be studied and where you can see.
Regulatory framework, practice

What concepts will we consider?
Electronic document
The electronic document is any information presented in electronic form:
- You photographed your car - this image is an electronic document;
- we sent a statement to the head of email - this is also an electronic document.
Any document can be translated into the "digit", but not every electronic document can be recognized without human participation.
Machine processing is more promising, so many documents can be divided into formalized and informalized electronic documents.
- Under an informalized document, we understand that a person looks at the photo and sees that the car number is so.
- And for formalized electronic documents, schemes are usually developed, where the composition of the fields, their limitations, binding, or optional, etc. is prescribed. Such formalized documents can be recognized automatically.
Perspective for formalized electronic documents. The departments are gradually moving to new rails. Many of them produce their regulations describing in which format can be exchanged information.
- For example, the arbitral trial accepts documents only in PDF format.
- And electronic invoices must be transmitted in XML format, and there is a special regulatory framework with a description of their required fields. Taxpayers who want to share invoices in electronic form should clearly comply with these requirements.
Previously, there was a problem that the FTS obliges to move to a new format of electronic documents is approximately the same as a new format of electronic reporting - from March 1 there will be a new format, and then "even the grass does not grow." Now, after a couple of years, they publish the format, waiting for feedback and then warn that it is necessary to smoothly go through this year. At the same time, both old and new formats are accepted in parallel. The tax service should always receive documents in any format, because documents can be five years old, and in electronic form they must still be accepted.
Electronic signature
Law No. 63-FZ introduces the concept of electronic signature. Previously, there was the concept of "electronic digital signature" (EDS), now it is more correct to use the term "electronic signature". There is a law three types of electronic signature.
- The first view is simple electronic signature. For example, when using a mobile bank, you receive an SMS with a one-time password, and you do confirmation - this is an analogue of a simple electronic signature. By such a signature, you can only determine the author.
- Second and third species is enhanced electronic signature. "Enhanced" means that some kind of cryptocution is used. Enhanced signature is divided into unqualified and qualified.
A reinforced qualified electronic signature is sometimes called simply qualified electronic signature (CEP). This is an electronic signature on the basis of a certificate, which is issued by an accredited certificate center. The Ministry of Communication is conducted by the list of certifying centers that provide electronic signature certificates.
Certificate of electronic signature (he can still be called an electronic signature key certificate) - it paper or electronic document, unambiguously determining who owns this signature.
Qualified electronic signature applies most widely. Its main purpose is that it confirms the authorship, guarantees non-closer and ensures the integrity of signed data. This means that if you signed an electronic invoice by a qualified electronic signature, then:
- You cannot say that this is not your signature;
- You can't refuse it (to withdraw);
- you can check whether changes made to this document after you signed it.
If talking pro Application of electronic signatures, It is worth dividing them to local and cloud.
- Local electronic signature - Situation when you sign any documents on your computer. In this case, cryptocution is required, the installation of the certificate is a lot of difficulties.
- Cloud electronic signature - The situation when you trust the warehouse of closed keys to a certain holder in the "cloud", and to sign the document, it is necessary to convey it before this cloud. Most likely, a disposable password will come to your phone to be confirmed. And after confirmation, the electronic signature will be formed on the server in the cloud, and you will receive a signed document.
FSB has released an explanatory letter in which explained that cloud electronic signature is not qualified. Therefore, if the law says that the document must be signed by a qualified electronic signature, and you have a document signed in the "cloud", then keep in mind that this may have problems - to this you need to approach very carefully.
What else can I tell an interesting legislation that will concern us?
- In 2016, a single certifying center of the Ministry of Communications of Russia appeared, which allows you to build a chain of trust up to any certificate. This head certifying center of the Ministry of Communications Communication, issues certificates to accredited certifying centers, and they are already issued to individuals and legal entities. Therefore, for any electronic signature you can always build a chain of trust. It is very convenient, because it used to be difficult to check in practice that the signature from another Certifying center of Validna.
- Most of the new - in early 2017, the Ministry of Communications made a legislative initiative to issue all qualified electronic signatures to give to the state monopoly. On this central bank and the Ministry of Economic Development, literally in July answered that it was impossible to do that, because it would take the jobs and destroy what was worked out for years. Most likely, this legislative initiative will not go further, but such a thought was.
Features of the use of EDO with EP in companies
What are the features of the use of electronic document management in companies? Please note that when you launch projects related to electronic signature and cryptography, consulting services are very important.
If a the company launches electronic document flow, then:
- the first task is prescribe the use of electronic document management in accounting policies;
- next need issue an order at the enterprisewhere to specify which faces can sign documents;
- if you exchange a counterparty, you must have an agreement in which it is written how you will cancel and adjust the documents. For example, if you do not like some paper document, you can agree with your counterparty and just break it, and everything will be fine. And in electronic form everything is more complicated, because the number of copies of the document you generated and signed may be unlimited. And even if you and your counterparty agreed to cancel this document, then its email equivalent is not enough to simply remove from your base. To adjust the electronic document or refuse it, you need to form a new electronic document on its basis, and already specify in it how your deal looks now. And only after you sign this new electronic document on both sides, the transaction information will be fixed in the form you need.
All this must be prescribed and use.
The readiness of the regulatory framework
I would appreciate the readiness of our regulatory framework - already there is some kind of "building", but it needs to be more accurate.
- For example, there is no understanding how we will check the electronic signature in the archive of electronic documents in five years. Because the certificate lives one year, and when its validity period ends, the signature will be vivend - it is not clear how to check.
- It is not clear what "signature date" is. For some accounting documents, it is important to know which time the document was signed. Now, when signing the document, you can "Mukhlove" - \u200b\u200btransferred the date of the computer, signed, and it will look like a document signed by "rear." Therefore, in order to unambiguously say that the document subscribed to then should be one of the options:
- or there must be a single center distribution of time tags, so that at the time of the signing of the documents we went to some federal service department, which would give us a time stamp for signature;
- or, when you exchange email invoices, there is another third link - this is an electronic document management operator. He misses the documents through himself and does not give a "dimness", because it generates its receipts (confirmation), in which the date and time is prescribed.
In general, there is where to move.
The mechanism of cryptography in the platform "1C: Enterprise 8"

The mechanism of cryptography in the platform appeared from version 8.2 - this is a fairly young mechanism. The platform itself does not contain cryptoalgorithms, it contains only calls and objects with which you can refer to cryptographic services on the computer:
- for Windows is CryptoAPI interface;
- for Linux there are no such interfaces, there is a direct appeal to cryptography modules.
From here it becomes clear that cryptography can be applied only if cryptocution is installed on the computer. And, on the other hand, that the "1C: Enterprise" platform itself is not required to be certified from the point of view of cryptography.

Main cryptographic operations in the 1C: Enterprise 8 platform:
- You know that the platform can work in different modes: thick, thin, web client, external connection and mobile application. In all these launch modes, cryptography is supported - For a mobile application, support for cryptographic mechanisms appeared from version 8.3.10. I would recommend to read the "Syntax Assistant" and watch which methods are available in one or another launch mode, because there are limitations.
- The platform allows you to work with open key certificates (X.509)which are installed on the computer. We cannot release a new certificate or request its release, we only work with what we have - using the platform mechanisms, we can find a certificate on a computer, read its attributes, unload it to a file and check how valid it is.
- I often came across my practice with misunderstanding how in the platform works encryption and decoding. This is especially important when you make integration with some external contractor, which is not working for 1C. When you encrypted the document, sent it to the other side, and there they try to decipher. For example, questions often arise if the GOST 28147-89 algorithm was specified when setting up a cryptoproder in 1C, which is symmetrical, and the decryption requires an appeal to the closed key. Let me remind you that the symmetric encryption algorithm implies that for encryption and decryption you use the same key. And asymmetric encryption is when the data is encrypted using the public key, and another closed (secret) key is used to decrypt. Contractors are asked: "But you said that the encryption algorithm is symmetrical, why then when deciphering you need a closed part of the key?" Let's figure out how the encryption mechanism works in the platform:
- a randomly creates a fixed length key, with which the data set is encrypted according to a symmetrical algorithm;
- then the key itself is encrypted by an asymmetrical algorithm using a recipient certificate public key;
- encryption using a symmetric algorithm works faster - we have been encrypted a large amount of data, and then the small key of the fixed length is quickly encrypted using an asymmetric algorithm;
- encrypted data, list of recipient certificates and the encrypted key itself are packaged in one PCCS # 7 specification package;
- this package is sent to the recipient side;
- and the decoding works in the reverse order.
- Signing and checking the electronic signature. When signing the platform tools, an appeal to the closed part of the key and the integrity check (mathematical validity) of the signature is built into the platform. From the point of view of the legal significance of this is not enough. If you want to check the electronic signature under the document, you must check:
- certificate;
- mathematical validity of the data you sent.
It is so done in the BSP mechanism - this will be discussed a little later. The platform does not.
Protected TLS connection for organizing an encrypted data exchange channel.Two versions of TLS - 1.0 / 1.2 are supported. The TLS version is set to the source with which you install the connection - if the source uses Protocol 1.2, then the platform will raise the encrypted compound 1.2. If a BSP is used, then when accessing a resource, in the address of which is registered "HTTPS", encryption is automatically switched on. If "HTTP" is registered in the address, then traffic is not encrypted. Another interesting thing I can say that before the encrypted connection was installed only on RSA algorithms, and now at GOST-algorithms too. Browsers are not supported by GOST algorithms, and the platform is already able. But not everything is so good, unfortunately.
I have already mentioned that the platform can work only with those cryptographic services that are installed on the computer itself. Accordingly, there is a limit - if you want to use cryptography, you must have some kind of cryptocution. Wherein Cryptustriality cannot be used in portable mode, it must be installed on OS. It would seem that there was a token with cryptustia to the computer, the platform worked with him - it would not work.
Electronic signature is generated only in PKCS # 7 format (Separate, external file), in another way the platform does not know how.
Some departments require signature format. Xmldsig - In a simplified version, the situation when in the XML file you can take a certain set of tags, sign them and put the signature in the next tag so that in one document there were several signatures. Platform does not know how to do this.
I would still noted that with the help of the platform, it is difficult to diagnose emerging problems.For example, there are cryptochement on the computer, there is a certificate, somewhere there is a closed part of the key, and if the platform starts to call it all and at some point something does not fit, it is simply given an error - what failed, and the operation has not occurred. What happened there, where the problem is incomprehensible. Therefore, there is where to move in this direction and platform, and crypturalities.
Cryptography in external components

To remove the restrictions on the platform, you can try to make an external component.
- For this purpose, the company "1C" has a whole methodology, it is posted on disk ITS at https://its.1c.ru/db/metod8dev#content :221:hdoc. Examples are attached to it, you can use.
- When developing an external component to you you have to make assemblies for all operating systems on which your clients work. Well, if you know in advance that you have 100 customers, and all 32-bit windows. If this is not the case, you should make assemblies:
- for Linux;
- for Windows (32 discharges and 64 digits);
- if your clients work through the browser, you need to make expansion builds for each browser separately.
- When operating it is even worse. You work with an external component, as with an object whose properties you know only. If during implementation you have made a mistake somewhere, the program code for interacting with this object will not be able to work.
- There is another problem - it is not clear how you will deliver this external component to the client. The client's platform is already worth it, with crypturalities, too, everything is clear, and now you wrote an external component that binds cryptural and platform. But where it costs this external component, as you put it with the client - it is not clear.
- You must maintain and update the program code. If you use your external component in a typical solution, it means that it all needs to be taken into account when updating it. And if a new version of the platform is produced, you must do everything.
- There are ready-made examples of external components. The most vivid example of my practice is an external component for Sberbank. More precisely, Sberbank produces an external component for the service "1C: DirectBank". This external component implements its own electronic signature format and installing an encrypted compound.
BSP subsystem "Electronic signature"

Now about how easier to work.
"1C: Library of Standard Subsystems" (BSP) is a ready-made typical configuration from "1C", a set of universal functional subsystems, one of which is called an "electronic signature".
Immediately I want to note that the BSP itself is a certain isolated level from the platform, which has software and user interfaces. The "Electronic Signature" subsystem implements a software and user interface to work with cryptography (encryption, electronic signature).

When considering the subsystem "Electronic signature" it is important to understand what is in it:
- Basic functionality, where it is implemented that it will never be touched if you want everything to work.
- And there is a special overridden part for developers such as we, where you can add something to work differently. If there is no something, I recommend writing to the guys who develop a BSP to launch the possibility of override into basic functionality, and then you can do what you need in a redefined part.
The number of objects in the subsystem is not very large, the directories are only two:
- "PROGRAM ELEKTRONNYEPOPIYSHIPS";
- "CertificateCelectricElectronic Posyaching".
But the number of code lines in common modules is very large - 11.5 thousand striches of code. And the work itself with the subsystem is not very simple.
How to embed an electronic signature subsystem?
Suppose you have some configuration, you decided that you need to embed this subsystem into it:
- first of all, you need to read on ITS, how to embed the subsystems;
- next - read the instructions for the subsystem (the chapter "Setting up and using subsystems in configuration development", subsection "Electronic signature") - the order of work is written there;
- it is necessary to familiarize themselves with the BSP demobaz with examples of the challenges of the electronic signature subsystem;
- and at the end, after you have built the subsystem, you need to check:
- there is an extended platform check when you embed objects;
- and there is still a separate processing for ITS "Checking the embedding subsystems of the BSP" - with the help of it you can check how you all embedded.
And if you have a configuration from scratch, you take the subsystem and write on it - you will update yourself.
How to test an electronic signature?
- For testing it is possible use self-signed certificate - Release it on your cryptural use from Microsoft, which is embedded in Windows.
- Or it is possible use external fusion. With the help of "Cryptopro" you can:
- download trial version from your site;
- order a test certificate through the test certifying center;
- install the root certificate of the test certifying center;
- download and put a list of certificate recall (SOS) from this UC.
Thus, "without getting up from the sofa", you will receive a test environment for working with certificates and cryptography. This can be used.
The main functions of the subsystem "Electronic Signature" from BSP

This is an example of a BSP demobaz. In the "Administration" section there are two functional options: "Encryption" and "Electronic Signature". If you turned them on, you can go to the settings.

The settings are two reference books: "Programs" and "Certificates". In "Programs", the system determines which programs are installed, and immediately shows that everything is fine or everything is bad. If you use some kind of specific cryptocution, which is not in the BSP, you can click the "Add" button and specify the parameters of the appeal to it.

If you are working via a web client, the BSP subsystem will prompt that you first need to install the extension to work with files and expansion to work with cryptography. It is very convenient because you do not need to customize yourself - the system will find an extension and will offer to put it.

Certificates can be added in two ways.
- The first option is "from installed on the computer." In this case, the dialog box opens, where we specify how we will use this certificate.

- And the second option - you can order the release of a new qualified certificate. Please note that the platform itself does not allow to order a certificate issue, and the BSP allows. The BSP made integration with the certification center 1C, which issues certificates of qualified electronic signature. You can go through the settings wizard:
- the system will prompt which documents to fill and print for the issuance of the certificate;
- it will be necessary to conclude an agreement with a partner who can conduct an identity card and transfer documents in 1C;
- after 1C receives documents, a certificate will be released;
- the system will find it and install it on a computer.
Thus, users without leaving the program receive a qualified electronic signature certificate.

The magic happens next - checking the certificate by diagnosing the correctness of the settings. This dialog allows you to check how correctly the cryptography on the computer is configured - the system will try to sign the certificate, check, encrypt, decipher. It is also possible to insert some additional diagnostics here.
If you or your customers have some problems, you run "diagnostics", and everything will be clear. If there are problems, as in the example on the slide, you can click on the error icon, it will show you possible causes, and will try to tell you what to fix.

How to make calls for signature and encryption / decryption You can view the example of the "Files" directory in the DEMO-database of the BSP or in "1C: Trade Management", "1C: ERP" - there is the same subsystem.
Services "1C-Edo" and "1C: Direct-Bank"

How is cryptography in services? The first service, 1C-EDO is a service designed to exchange legally significant electronic documents through friendly operators of the company "1C".
- Client functionality is developed in the "Electronic Document Library".
- When trying to connect to the server, an encrypted SSL connection occurs (by https) on the RSA algorithms.
- Using authorization with cryptography. Since the server does not know about us, you are sent to the encrypted token, and if you are "the right" person, you decrypt this token using a closed key and use it later to exchange data.
- It is possible to view an electronic document, sign it, check, pack in the data package and send.
- Check and generally all cryptography works through BSP. An electronic signature check is performed in two stages:
- first, the validity of the certificate itself is checked: the validity period, the trust chain, attributes;
- if everything is fine with the certificate, then the calculation of mathematical hash is performed. If everything is fine with mathematics, the signature is considered valid and applied to the document.
- Also, using BSP implemented an extended diagnostics of EDO settings - it is determined that the servers are available, and that the participant of electronic document management is all in order - he has active tariff plans, etc.

The second service is "1C: DirectBank." Its appointment is exchange with banks by electronic documents directly, bypassing the client-bank program.
- This service is also supplied in the "electronic document library".
- Open DirectBank technology is described on GitHub.
- From the new - the encrypted communication channel with the service can be raised on the GOST algorithm.
- The exchange setting is made like this: 1C makes a request to the bank to get settings for a particular client. If necessary, along with the settings, the bank sends an external component, which is used with further exchange (so implemented by Sberbank).
- Authorization is made either by encrypted token, or by SMS (through a single password).
- Signing and verifying the electronic signature works either through the BSP or through external components (depending on how the bank itself implemented).
- And the diagnostics here is even more interesting, through the full cycle of the exchange of electronic documents of a special type - "request-probe".
- The 1C system is logged in in the bank system and transmits an electronic document to its signature there;
- The Bank checks the electronic signature of the client, forms notice that everything is well and signed by his signature;
- The notice arrives in "1C", she checks that the signature of the Validna bank and says after that that everything is in order.
This is such a mini-cycle - it becomes clear how much the exchange with your bank is correctly configured.
Own solutions with cryptography on the 1C platform
How to develop your own solutions with cryptography?
You can create a configuration from scratch - open the "Syntax Assistant" and use the capabilities of the Platform for cryptographic operations. But I would recommend using BSP - there is already a lot of what is written. In this case, you will need to write not 11 thousand lines of code, but smaller. But five thousand lines of code - for sure.
How to test - I already told. You can get a test certificate and try to work.
If you have developed a configuration from scratch - you accompany it yourself. And if you used when developing a BSP, and it released some new opportunity, then you can update the BSP subsystem and try this opportunity. The difficulties will be in any case, because the "silver bullet" is not here. I would approach the assessment of whether it is worth it or not to invent something, depending on the task you want to solve. Considering a specific task, you already choose: your solution or standard BSP based on the basis.
An example of its own solution is the development of the IT Industry partner. They developed a small module for internal electronic document management based on "1C: UPP". There, based on the printed form, an electronic document is formed, which is attached to the document of the information base, and it is possible to sign it with an electronic signature. A simple document flow within the company, but must accompany it anyway.
Difficulties in the introduction of cryptography and EP in organizations

What are there main problems?
- If you need to install on one computer two cryptocution, conflict will occur. For example, if you have reporting through ViPNet, and an electronic document flow with counterparties through "Cryptopro". How to solve this problem?
The first option is to dissemble these cryptochements on different computers.
If it is impossible, then for one of the services you need to release a certificate on another cryptocution - when you order a certificate in the certificate center, you can specify that for what cryptographic need you will use it.
- Sometimes at customers cryptography in IE browser does not work - It is required to establish an extension, but it is not put. Banal Council - run the browser on behalf of the administrator. This will allow you to establish an extension, and the problem will be solved.
- Program 1C does not always see jacard tokens. I do not know what the problem is, or in Jacard, or the platform. We reinstall cryptochement - it works for a while, and after rebooting the system flies again. For some reason, 1C and Jacard are not very friendly.
- There is another problem - when checking certificates, the platform is always trying to check how reliable, and sometimes it does not succeed. Why is this happening? There is a list of reviews where invalid certificates are included. For example, when an employee quit the company, it must inform the certifying center that the employee quit, and its certificate is not valid. After that, the certifying center releases a list of feedback, which includes this certificate, after which it begins to be considered invalid. Sometimes for some reason, check the certificate in the reconference list fails. What is the problem? These lists of reviews for 1c do not have any relationship, they are updated automatically by cryptographic. To do this, a stable channel must be configured to the certificate. If the list of feedback is not automatically updated, this means that the service is not sufficiently coordinated in the certificate center, or it is generally absent. Change the certifying center, and the problem will leave.
- When certificates become a lot (for example, more than 30), difficulties begin. Suppose you translated the business to electronic rails, and in the midst of the working day it turns out that the signature of invalid, because its certificate is over. The issuance of the certificate takes some time, the business "on the ears", you too. For such cases you need to use a specialized software to keep certificate list. There are programs that allow you to monitor the life cycle of the certificate, and when it does the validity period, they send a reminder to the administrator. This is a banal option, but it allows you to more or less streamline certificates.

- Exchange with data from 1C occurs from servers, so:
- open ports on 1C: Enterprises: Enterprises;
- the rights of the server account must be "Internet access";
- if you have a server cluster, it means that all 1C servers included in the cluster must be opened ports.
- If there is no confidence in the external resource, there is a separate article on ITS "Diagnostics of the problem" remote node did not pass the check "".
- Basic security rules:
- passwords on stickers do not store;
- working, take out tokens from cars;
- regularly update the antivirus.
Otherwise it turns out that you have set certified cryptocution, keys, and around the viruses that can take advantage of it. Therefore, protect the perimeter.
Information sources
Questions
I would recommend using the certifying center with which you will continue to work in terms of exchange of electronic documents. An example is an operator of electronic document management "Taxa", it has a certifying center. If you run an electronic document flow through "Taxa", it makes sense and for the certificate to contact them.
You said that the FSB gave some explanation about cloud certificates. What if the certificate is not stored locally, but in the cloud, it cannot be considered strengthened. In the case of a standard exchange of invoice and UPS, we can use the cloud certificate or is it necessary to use it all the same?
The law says that when exchanging invoices, an increased qualified electronic signature is required, so the cloud is not suitable here. But for other types of electronic documents - please.
Roughly speaking, for any standard EDO that we use in 1C, we need a reinforced certificate?
No, not for anyone. The law is written only about electronic invoices. They must be signed by a qualified electronic signature. Regarding the rest of the documents nothing is written. This means that for invoices, for orders you can use a reinforced unqualified electronic signature - including in the cloud.
And about the stop there is nothing? In fact, the UPB is now the same as the invoice.
There is a blurred definition - an invoice with advanced indicators, but this is not the same as the UPD. Therefore, I think that the UPD gets into the discharge of an unskilled electronic signature.
And what function in the whole chain is the operator - "1C-Edo" or "Taxi"? Usually through the operators, we send documents to government agencies and exchange invoices, and when exchanging other documents with counterparties, why do we need an operator?
Operators on the market are also not the first day, the invoices go through them. They say that - you send one invoice, and two other documents are free. You still will exchange invoices by invoices through them, so it's easier and the documents themselves also send them through them. Another thing, if you sit on a simplified, and you do not have invoices, then you can ask the operator to search for you an inexpensive tariff plan. And so in the same "electronic document library" there is an opportunity to exchange documents with an electronic signature by email, via FTP, etc. But when you have 100 counterparties, organize for each of them your communication channel will be difficult in terms of accompaniment.
And if we want to test a self-signed certificate, we can test any exchange using a self-signed certificate through the operator?
No, through the operator - no. If you really want to test, write to the company "1C" that you want to connect to the Edo service to test.
They say we are not a certifying center.
Write me, I will help.
And if we exchange without an Edo operator, I bring a signed electronic document, and I want to download it in 1C to keep it there. In BSP, there are enough funds to check that it is the CEP and it has the right details so that all this is in automatic mode without modal windows, etc.?
I did not meet such cases in our practice, but in BSP it is exactly possible to upload the file and check its electronic signature. Most likely, you will need just for this script to draw some kind of master: check the folder, pick up the document, take the signature, check it all, put it where and say that everything is OK. Regarding the synchronicity of the call - all this is implemented in BSP, everything in browsers works in asynchronous mode.
And if in 1c over the terminal to work? Is it possible to put "cryptopro" and in the terminal we argue the keys for him? What are the features, problems? And, accordingly, if we have more than 20 legal entities and for each of them two keys, how is the delimitation of rights to these keys go? At level 1c or how?
In the BSP itself, when you ship the open part of the key, it is possible to specify which user it will be available. You can, entering your name, see only your certificates. But at the same time they will all be on the computer itself. Therefore, you know, install the closed part into the registry is not necessary, because the closed part of the key is transferred without any problems with the car on the car. Better use tokens. It is possible to break the token with a closed part of the key to the terminal server. Key manufacturers' guys help themselves to configure it so that this key is visible in the terminal. Try, experiment, find other keys, find people who help customize. But here you need to understand that this tunnel from the terminal server before your key is not safe. You generate an electronic document on the terminal server and say - sign. What happens? There is a data transfer over an unprotected channel first to a local computer where the key is installed, an electronic signature is generated, then the data is transmitted back to the terminal server. But this channel is not protected. It can only be protected by installing a specialized software that makes the tunnel between the terminal server and the local machine safe. If you want to work safely, it means that you need to put a token, we break it up to the terminal and put the software to encrypt the channel between the terminal server and the client machine.
Tell me, is there any difference in speed between the signing of an electronic invoice and a scanned contract in 100 pages (where purely graphics).
The more the document, the more slower signs, because asynchronous encryption is there - the Hash is calculated using an asynchronous algorithm. But from the point of view, whether you sign an electronic invoice in several lines or 10MB file - visually the difference you will not notice. Note only on volumes in 1000-3000 documents.
Regarding the roaming of 1C-Edo. In the "Taxa" there is roaming between operators. And how much is it workable in "1C-Edo"? Do you have such an experience? Because all the counterparties are sitting on different operators and choose the operator with a maximum coating is very difficult. Who would you advise?
If you choose between "1С-Edo" and others, then of course, "1C-Edo." But "1C-Edo" has some roaming problems - it is not so many operators support. There is a separate resource for 1C-Edo, there is a list of supported operators, I think that it has to be replenished with time.
And where to store the archive of signed documents? Locally in the company or in the cloud? Is it possible to ensure the validity of the documents persistent in the cloud?
Where we store signed documents (in the cloud or not) - no matter. Mathematically hash is already calculated, and the contents of the document will not change without a trace. You can then pass it at least 10 times somewhere, the signature can always be checked purely mathematically. If the cloud service is convenient - please keep it, it is probably even more interesting.
And the operator provides such a service?
If a separate contract with him to put backups for storage - they do it for individual money.
Are they not stored for signed documents?
Physically, they are stored, but according to the law they are not obliged to store them. They are obliged to store only the receipt. If the tax will come to them and ask - whether such a document passed, they will show, yes, here is a receipt, look - such a signature. And what is there within this document - this is no longer a question for them.
And for the UPP, the operators do not provide any processing for Edo?
I can't say about the operators, there are many of them, and everyone has its own developments, but in the EPP itself, there is an electronic document flow.
****************
This article is written in the results of the InfoStart Event 2017 Community conference. More articles can be read.
In 2020 we invite everyone to take part in 7 regional allocations, as well as the anniversary InfoStart Event 2020 in Moscow.
The electronic signature (hereinafter - EP), according to the Federal Law of the Russian Federation No. 63-FZ of March 25, 2011 "On Electronic Signature", is defined as information in electronic form, which is attached to another information in electronic form (information signed) or otherwise Related to such information and which is used to determine the person signing information. The specified regulatory act came to replace the legal force of the Federal Law of the Russian Federation No. 1-FZ of January 10, 2002 "On Electronic Digital Signature" from July 1, 2013.
The Law of March 25, 2011 allocates two types of EP: simple and reinforced. The latter can be qualified or unqualified. If simple EP confirms that this email is sent to a specific person, then the reinforced unqualified EP allows not only to uniquely identify the sender, but also confirms that no one has changed it from the moment of signing the document. In the future, we will discuss the reinforced unqualified EP. A message with unqualified EP can be equal to a paper document signed by itself, if the parties agreed on this in advance, as well as in the cases specifically stipulated by law.
On the one hand, EP is used to confirm the authorship of the document - in this its value for the sender of the document. On the other hand, an electronic signature in the case of recognition of its legal significance ensures the unusability of the author from the signed document, which in turn is important for the recipient of the document. In the case of a controversial situation, conflicts can always be carried out, which will unambiguously determine the author of the signed document and will force him to be responsible for the signed document.
Relationship of conflicts associated with EP
The main problem with the analysis of conflicts of sports situations on documents signed by EP is the proof of the fact that "information in electronic form, which is attached to another information in electronic form (information signed)" is a legal and significant EP of a particular person under a specific document.
The use of cryptographic methods allows you to solve this problem. If a person is issued a unique electronic key and then produce special transformations using this electronic key and an electronic document, then the result of these transformations (and this is EP) will be unique for this pair (key document). Thus, the task of the first stage of conflict parsing is to identify whether this signature was developed using this electronic key or not - is solved by cryptography methods.
The second stage of conflict parsing is to prove that this electronic key is the property of a particular person. This proof gives EP legal significance. To solve this organizational task - accounting of the issued keys - the PKI (public key infrastructure) is used.
Giving EP legal significance with PKI
In the Law "On Electronic Signature" distinguish the EP key and the EP verification key. The electronic signature key is a unique symbol sequence designed to create an electronic signature. On electronic signature check is a unique character sequence, uniquely related to the electronic signature key and intended for an electronic signature authentication. The check key is epusodes from the key EP, but the reverse operation is not possible. Thus, there is an unequivocal compliance between the EP key and the key test key. The EP key should be created by the client himself and are kept secret. It is this key that serves to sign the documents by an electronic signature. The EP verification key serves to verify EP and distributes to everyone to check the signature.
The main element of PKI is a certifying center. The certificate center contains the register of compliance of keys and persons who are owners of these keys. To register the key, the client refers to the UC open part of his key along with its identification data and receives a certificate of conformity certifying its possession of this particular key. The certificate of conformity contains the EP check key and the customer identification data, and is signed by the EP certifying center. Thus, the UC certifies that this client was checked and is the one for whom it gives out. Upon receipt of the Certificate, the client in turn signs special documents on the reliability of the certificate issued by its manual signature. These documents are the main connected link between a particular person and the "set of electronic characters", its EP.
Thus, it is enough to check the signature and identification of the signed certificate of the signed. That is, the Subscribe signs the document with its EP key, and then sends this signed document to the recipient and its certificate containing the EP verification key. In this way, the recipient will be able to verify that the signature was indeed made by the EP key signed and receive identification data to the signed from the certificate. The client must protect its EP key from compromising. It is for this purpose that various hardware key storage facilities are created with an increased level of protection, for example, a USB device Rutoken.
Russian standard EP.
ED standards are two-level. At the first level there is directly EP from the document. The second level includes EP and all documents necessary to give EP legal significance: a certificate of signed or a chain of certificates, the creation time of signature, etc.
The Russian standard EP of the first level is GOST 34-10.2012. The Russian standard EP second level is PKCS # 7 with the possibility of adding TSA temporary tags.
Scope of EP
- internet bank
- electronic marketplace
- corporate document management systems
- delivery of reports to various federal services
- copyright
Web site with EP
Formulation of the problem
Suppose in your organization decided to switch to the electronic document management system built on Web technologies. At the same time, the main places in which EP is required are:
- EP files of an arbitrary format when downloading them to the Web site by the user through the input form
- EP text data entered by user in the input form on the Web site
- EP Posted on the Web site of the document by several users
- cryptographic data protection between the workbirth of the user and the Web site
- user authentication for digital certificate to access his personal account
- cryptographic protection stored on the server information
Schematic solution
Creating a certifying center
select the server on which the certifying center will be deployed. Optionally, temporary label and online verification certificate status can be deployed. The CAC and the specified services for savings can be used by one server, which should be available online. The feasibility of these services we will discuss below.
install the product Magpro cryptopacket
create a key of the UC and the application on the root certificate of the CCM using the MKKEY utility from the MAGPRO cryptopacket. The key can be created on a secure device, for example, on Rutoken. After creating a CC key, it is required to ensure its security by organizational methods. The most secure option is to store the key on the RUTOKEN device and fed it to the server only when issuing certificates. CERTIFICATE CAC is a file. This file will subsequently be issued to all CCC customers upon receipt of the certificate.
create a root certificate of UC using the OpenSSL utility from the MAGPRO cryptopacket.
create the directory structure in the file system in which you will be stored as files issued user certificates issued servers certificates, certificate applications. It is followed by organizational methods (for example, using ACL) to ensure the right access rights to these directories. Certificates will be issued as files in PEM format. It should be borne in mind that the names of the certificate files are best understood in order to further facilitate the task of finding certificates.
Creating a key and PKCS # 10 applications for certificate
To obtain a certificate, the UC user can use two schemes: centralized and remote. With a centralized scheme, the user comes to the CC and give it a file in which the key and certificate are located. Then it adds this file to the USB flash drive. This scheme is simple and convenient, but unsafe, as it allows you to find out the user's key to employees of the UC. But in some cases, the use of this scheme is incredible.
The most secure scheme for obtaining a certificate is distributed. The user creates the key, creates a PKCS # 10 application for a certificate that contains its EP check key and identification data. The user signs this application with its EP's key and refers to the UC. The CCC checks the signature under the application, the user's identification data is checked, for example, with passport and issues a certificate. Then printing certificate and the user signs a manual signature document on the compliance of the certificate issued.

As part of the decision under discussion, the key generation and the creation of an application is made using a special program from MAGPRO cryptopacket. This program enters the user set of cryptotunnel.
This program has a flexible configuration system, with which you can create applications for completely different types of certificates, extend the standard set of identification information, add role and user rights to certificates, for example, to delimit access to Web resources; Add to the application various attributes.
After creating the key, the user must ensure its safe storage.
Types of certificates for EP on the Web site
Several types of certificates will be used in our portal:
root certificate UTS
This certificate is used to check all other certificates of the participants of the Web portal.
server TLS authentication certificate
This certificate is used to verify the server by the client when creating a secure TLS connection when transferring signed documents to the Web site
certificate of TLS-authentication of the client
This certificate is used to check the client by the server and to access the client to its personal account when creating a secure TLS connection when transferring signed documents to the Web site
certificate EP Customer
This Certificate The Client adds to its ES, and thus the testing party can check the signature and identify the signed
oCSP Server Signature Certificate
This certificate of the OCSP server adds to its signed response to his certificate
tSA Server Signature Certificate
This TSA server certificate adds to its signed response to his certificate and give it legal significance
All these types of certificates can be created using a UGPRO cryptopacket utility and UC based on Magpro cryptopacket.
Obtaining a certificate in UC
When receiving an application from the user, the UC administrator creates a backup copy of its application. Then checks the application and using the OpenSSL utility creates a user certificate, signs it on the CCT key and also provides its backup. In addition, to ensure legal significance, the administrator makes a printout of information from the certificate (obtaining this information is provided with the OpenSSL.EXE utility) and receives the user's manual signature under this printout. Then gives the user to his certificate in the file.
So, at the moment we were able to deploy a UC and learned how to create user keys, accept applications for certificates and issuing certificates for received applications. Obtaining and compliance with the certificate, the user certifies its manual signature, and therefore it can be argued that we are deployed by PKI, which ensures the legal significance of the user's EP
The next task is to use the deployed PKI to solve the applied task - the organization of safe transmission using the browser signed electronic documents on the Web site and receive them into the processing on the Web site.
EP check and storage module (server)
Usually the Web site is deployed on some web server (Apache, IIS, Nginx, etc.). This site contains a personal account for each user, which is registered on the site. To access the personal account, the user must pass the authentication procedure. Usually authentication is to enter a deign and passwords agreed upon to register the user.
In addition, a Web form of input is used to download electronic documents to the server.
In order to "fasten" the EP control to this system, to protect the connections between the user's browser and the site, as well as provide rigorous user-to-access user authentication to access the Personal Cabinant to the server, you should install the Magpro Crypt Server product.
Architecturally, the solution will look like this:
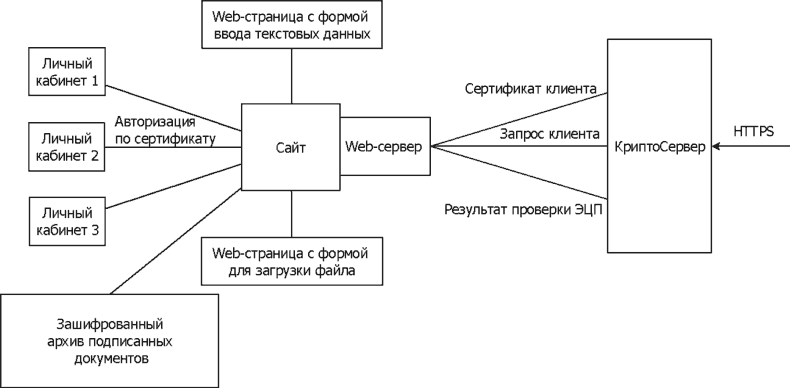
The cryptoer is installed before the protected WEB server. At the same time, the Web server is configured in such a way that it takes incoming connections only from the crypto server (see the setup instruction). The cryptoerver accepts incoming HTS connections, decrypts them and forwards to the Web server. In addition, the crypto server adds the X509-CERT header request to the HTTP request, which transmits the client's digital certificate that has passed the authentication procedure. This certificate is then used to access the client to his private account. To verify EP under the transmitted documents, the crypto server includes the OpenSSL utility, which allows you to check the original types of signatures, obtain from the envelope PKCS # 7 certificate signed or chain of certificates, etc. To check the EP, the Web page of receiving documents should make a call to this utility.
ED Development Module (Client)
The main task of the user when accessing the Web site is to load electronic documents and text data to the site, as well as downloading electronic documents from the site. To protect the WEB connection with the SSL / TLS site and for online signatures of data transmitted to the site, cryptotunnel should be used on the client workstation.

The main advantages of cryptotunnel:
- provides protection of WEB connections between any browser and SSL / TLS protocol site with the support of Russian cryptoalgorithms
- loads authenticate user by digital certificate to access the user's account.
- allows you to sign ONLINE documents when downloading to the site without using CSP and Active X
- supports Online Certificate Status Check (OCSP)
- supports receiving trusted temporary tags under EP (TimeStamp)
- supports various USB-tokenes and smart keys storage cards
- does not require installation in user locations, distributed by copying
- can be stored on a conventional flash drive and run from it
- does not require system administrator rights
- supports working with any Web browser (Internet Explorer, Mozilla Firefox, Google Chrome, Opera, Safari Apple, etc.)
- does not have "binding" to one computer - the user can use one set for use in the office and houses - cash savings
- has a simple and understandable user interface, which allows you to do without user learning
- allows you to minimize the cost of technical support for users
- can work on a large spectrum of operating systems (cross-platform solution)
These are all the actions you want to make cryptotunnel to start signing data and files transmitted via the Web form. It is not necessary to write any additional scripts, call Active X, etc.
Organization of multiple EP
Multiple EP is required if the document must be signed by several persons. In this case, the document is usually postponed on the site so that it is available only to users whose EP is required. This access separation is collapsed using user authentication by digital certificate.
When using cryptotunnel, the user does not have to download the document, and then sign and download the document to the server again - all these operations cryptotunnel will automatically press the button on the web page.
Service OCSP.
It often happens that the HC recalls the user's certificate (for example, if the user's key was stolen by an attacker). At the same time, the rest of the users must be notified of the revocation of this certificate, so that they stop him trust. There are several ways to notify users about the revocation.
The easiest way is the distribution of recall lists (CRL). That is, the CAC creates and periodically updates a special file that users also periodically download.
Another way is to use the online certificate status check service - OCSP services. To verify the status of any certificate, the cryptotunnel and the cryptoerver automatically form an OCSP request, send this request to the service on the network. The service checks the certificate, signs the result of checking your EP and returns the answer to the client. The client is watching the answer, checks under it a signature and makes a decision - to trust this certificate or not.
Creating an OCSP service is possible using the OpenSSL utility from the MAGPRO cryptopacket. It should be borne in mind that the choice between CRL and OCSP always remains at the discretion of the creators of the site. CRL - a little cheaper, OCSP - a little safer.
It should be canceled that the cryptotunnel and crypto server support both OCSP and CRL.
TSA temporary tag service
The main purpose of the temporary label service is to confirm the fact that the document was signed by EP no later than the time specified in the timestamp.
To create a temporary mark, cryptotunnel creates a TSA request to which the hash applies from EP; Sends this request to the TSA service. The TSA service adds to this hash current time and signs the result of its EP. Thus, a trusted temporary label is created.
To create an online trusted temporary tags, use the Magpro TSA product. In this case, the URL of the temporary tag service is set by the Web page on which the Web form of the signature is
The TSA client part is built into cryptotunnel. Upon receipt of the timestamp on EP, all actions are automatically produced, without user attracting.
Arbitrator
The referee is a special program that is used when analyzing conforms by EP.
The referee allows you to visualize certificate identification data, which is in PKCS # 7 signatures; Visualize the chain of confidence and the time of creating EP (TimesTamp). To parsing the conflict, the arbitrator checks the signature under the specified document and reveals whether it was produced by the owner of the certificate.
It should be noted that for the very possibility of parsing conflicts, documents and their signatures should be stored in an electronic archive for a long time.
Protection of personal data on the Web site
The data that exchanges between the client's browser and the site may contain personal data and confidential information. If all users of the site are interested in protecting confidential information, the protection of personal data is the requirement of the Law of the FZ 152-FZ "On Personal Data".
When using the site, the data is subjected to a threat when passing them through the Internet and when they are further stored on the site server.
Protection when transferred between the client and the server
The Internet is an unsafe information transmission channel. The main threat when transmitting data via the Internet is the attack "man in the middle", that is, an attacker connects to the line between the client and the server and replaces the transmitted information. The only way to protect data in the Internet is encryption of this data. Since encryption is a cryptographic way to protect information, then the requirements of the FSB are applied to it to the means of cryptographic information protection - the availability of the FSB certificate.
For cryptographic protection of connections between the user's browser and the Web site (Web connections), the SSL / TLS protocol is used. Kryptotunnel provides data protection on this protocol fully relevant to the requirements of the FSB. Thus, Kryptotunnel is a certified solution that fully meets the requirements for technical means of protecting personal data.
Protection during storage
When storing data in an electronic archive of the site, these data should be stored in an encrypted form. Creating a secure electronic archive is a subject of a separate article.
Basic concepts
KSKPEP
-Bedified electronic signature check key certificate.
CEP - Qualified electronic signature.
Cryptoprovider – cryptographic protection tool for information. Program with which the closed part of the electronic signature is generated and which allows you to work with an electronic signature. This checkbox is automatically affixed.
Exported key – the ability to copy an electronic signature to another medium. In the absence of a check mark, copying an electronic signature will be impossible.
LKM. - Left mouse button.
PKM. - right mouse button.
CRM-Agent. - An application developed by CC specialists to simplify the procedure for generating a key pair, creating a query and write certificate.
After visiting the certifying center and passing the procedure for reconciliation of the personality, the email specified in the statement, the UC sent a letter containing a link to generate. If you have not received letters, refer to your manager or technical support for UC on the contact number from this manual.
Open a link to generate from the letter in one of the recommended browsers:Google Chrome., Mozilla Firefox., Yandex.Browser. If you are already in one of the above browsers, click on the link LKM. or PKM.\u003e "Open the link in the new tab." Generation page (Fig. 1) opens in a new window.
When opening the link, the initial warning will appear. Check out it if you use the carrier to store the CEPJacarta. Lt. . More about media in below. If you use another media, press the button. "Close".
Fig.1 - Generation page
Click the link"Download app" To start loading. If nothing happened after clicking, click on the link PKM. > "Open a link in a new tab". After downloading the application, start the installation.
It is recommended to disable antivirus software before loading the program. !
In the process of installing the application « cRM. - agent. » A message will appear with the access request (Fig. 2).
Fig.2 - Access request

Press the button "Yes".
After installing the application, go back to the generation page. A message appears about "providing access" (Fig. 3).
Fig.3 - Access to the repository of certificates

Click "Proceed" and, in the window that appears, "Provide access"(Fig.4).
Fig.4 - Access to the repository of certificates 2

If the button does not appear "Proceed"
If after installing the application « cRM. - agent. » The link to download the application did not disappear, the reason may be blocking the connection of your security system.
To eliminate the situation you need:
Disable antivirus installed on your computer;
Open a new tab in the browser;
Enter the address without spaces to the address bar of the browser - 127.0.0.1:90 - and go (clickENTER on keyboard);
When a browser message appears "Your connection is not protected", Add a browser to exclude a page. For example,Chrome.: "Additional" - "All the same go to the site". For other browsers, use the appropriate developer instruction.
After the error message appears, go back to the generation page and repeat Point 2 This instruction.
In case you have no pre-installed cryptoproders, after the access phase, references will appear for downloading cryptopro (Fig. 5).

It is important: attachment « cRM. - agent. » detects any cryptoproprodes on the computer, and if you have a different from Cryptopro CSP Program (for example,ViPnet. CSP ), contact technical support specialists for consultation.
Click the link "Cryptopro 4.0" On the generation page or similar link below to download the cryptopro installation file to the computer.
CRPTOPRO CSP 4.0 - version for Win 7 / 8/10
After the download is completed, openzip.- Archive with the appropriate archiver program (for example,WIN. - RAR ). Inside there will be a cryptopro installation file. Run it and set the default settings. During the installation process, you may have the following window:
Fig.5 - installation of cryptopro

Skip the window by clicking "Further". Installation of cryptopro completed.
Signatures can be stored in the registry of a computer, on ordinary flash drives and on specialuSB- Centers. List of tokens, PIN codes and references to software are presented in the table below (Table 1).
Table 1 - Drivers for protected media
|
USB media type |
Exterior USB carrier |
Link to download drivers |
PIN |
|
rutoken. |
 |







